Even if moving files between two computers is extremely simple, occasionally there may be issues. For instance, if we use two systems, they might each have a different directory structure, different ways of representing data or text, and different file conventions.

File transfer protocol, also known as FTP, is used to solve this issue by creating two TCP/IP connections between hosts (client & server). Data has primarily transferred over one connection while being controlled over another. Consequently, this article offers a file transfer protocol, or FTP, overview.
What is FTP (File Transfer Protocol)?
To transfer files between two sites from client to server through TCP/IP (Transmission Control Protocol/Internet Protocol), the FTP or File Transfer Protocol is a common internet protocol (IP). In TCP/IP, this protocol is regarded as an application layer protocol. FTP enables file sharing across systems, promotes usage of the remote computer, and transports data more effectively and dependably.
Types of File Transfer Protocol
The following sections explain the various file transfer protocols, including HTTP, FTPS, HTTPS, SFTP, SCP, WebDAV, WebDAVS, TFTP, AS2, OFTP, and AFTP.

- HTTP
For the transport of business files, HTTP (Hypertext Transfer Protocol) is a widely used protocol. Particularly for file transfers from client to server and client to client, this protocol is quite easy to implement. Like FTP, HTTP is also susceptible to firewall problems, however, unlike FTP, this protocol is fundamentally insecure and unable to secure data or adhere to legal requirements. Therefore, where security is not an issue, this protocol is employed.
- FTPS
File Transfer Protocol Secure, which is identical to HTTPS, is the safest version of FTP. TLS (Transport Layer Security) and SSL, or secure socket layer, are used to protect these protocols. Businesses may communicate securely with their clients, business partners, and users thanks to FTPS. FTPS-based applications like client certificates and server identities are used to simply exchange and authenticate the sent data.
- HTTPS
The most common protocol used for data transmission between a website and a web browser is HTTPS or Hypertext Transfer Protocol Secure. To improve the security of data transport, this protocol is encrypted. Therefore, if consumers move sensitive data like bank account logging, health insurance provider, or email service, this becomes particularly important. The website where users must log in must be HTTPS compliant. Different Web browsers take the use of HTTPS seriously, but some will mark all websites that are not HTTPS-based as unsafe.
- SFTP
A secure file transfer protocol called SSH File Transfer Protocol (SFTP) runs on top of SSH and provides all of SSH’s security and authentication capabilities. This protocol has quickly supplanted FTP/S as the standard for file transfers. With a straightforward configuration, it provides all the functionality provided by these protocols more securely & reliably.
By encrypting data and using cryptographic hashing methods, SFTP protects against assaults, password sniffing, and data dependability while also authenticating the server and the user.
- SCP
SCP is an older form of the SSH File Transfer Protocol (SFTP), which is based on SSH and has comparable security characteristics. However, if you are using a recent SSH version, you already have access to SFTP and SCP. SCP is only necessary when exchanging files with a business that only has a legacy SSH server because SFTP provides greater capabilities than SCP does.
- WebDAV
HTT-based Web Distributed Authoring and Versioning (WebDAV) is primarily intended for collaborative tasks. Users can collaborate on a single file while working from separate places using this protocol, in addition to exchanging multiple files. Therefore, this protocol is appropriate for many companies like research institutions and universities that need dispersed authoring capabilities.
- WebDAVS
WebDAVS is the HTTPS-based variant of WebDAV, whereas WebDAV operates via HTTP. Therefore, it displays similar WebDAV traits, including the safe SSL features.
- TFTP
Trivial File Transfer Protocol, or TFTP, differs from other protocols because it may be used for a variety of network management activities, including booting the network, backing up configuration data, and installing an operating system via a network. X-terminals, diskless workstations, and routers can boot up using this high-level protocol for data transmission (User Data Protocol).
- AS2
The AS2, or Applicability Statement 2, is designed for Electronic Data Interchange (EDI) operations, which are frequently seen in the manufacturing and retail sectors. Today, EDI is used in healthcare as well. If you operate in these sectors or need to do EDI transactions, this protocol is a great option.
- OFTP
The Odette File Transfer Protocol, or OFTP, was created specifically for EDI. This protocol is widely used, particularly in businesses in European nations. For B2B transactions, AS2 and OFTP are the best protocols because they are both inherently secure and even enable electronic delivery receipts.
- AFTP
The JSCAPE-developed AFTP, or Accelerated File Transfer Protocol, is intended to accelerate file transfers across high-speed networks that are unable to fully exploit network throughput because of high latency and packet loss. When compared to FTP and other file transfer protocols, AFTP can speed up file transfers by up to 100 times.
How Does File Transfer Protocol Works?
The FTP mechanism is displayed below. In order to exchange and manipulate files via a TCP/IP-based network, such as the Internet, FTP is a common network protocol. This protocol was developed using a client-server architecture. The client-based applications and server-based applications in this architecture employ distinct data and control connections. In order to prevent unauthorized user access, this protocol is used for user-based password authentication.
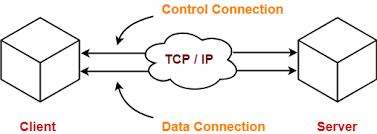
Although the data transmission between systems is very simple and easy, it occasionally runs into problems. For instance, the file conventions between two systems could be different. Therefore, text and data may be denoted differently within these two systems, and the directory structures of the two systems may differ. By establishing two connections between two hosts, such as a client and a server, this protocol solves these issues. One connection is primarily used for data transmission, while the other is used for data control.
FTP connections come in two flavors: control connections and data connections, which are covered below.
Control Connection
In FTP, the control connection is primarily used to transmit control information such as user IDs, secret codes, and commands for modifying distant directories and for retrieving and storing files, among other things. On the server, port 21 is merely used to establish this connection. The control processes are connected by this connection, which is kept open throughout the FTP interactive session.
The features of control connection include the following.
- The control connection helps the client and server communicate control signals.
- Only the client and server’s control process, also known as the Protocol Interpreter or PI, uses this type of connection.
- The well-known FTP server port 21 is used for the TCP connection for the control signal.
- Throughout the duration of the FTP interactive session, this connection will remain active.
- Simple communication rules are used in this kind of connection. As a result, we must only communicate one line of response and one line of command at a time.
Data Connection
The actual file and folder are transmitted using this protocol via a data connection. This link is also referred to as a separate connection. This connection, which is opened and closed for each file transmitted, links the various data transmission processes.
When a user initiates an FTP connection, the control connection is first formed; while this connection is active, the data connection is repeatedly opened and closed in order to transfer server files.
The features of data connection include the following.
- The fundamental purpose of this link is to transfer actual data.
- This type of connection is easily formed between the client’s and server’s DTP.
- The server port of Port 20 is used for data connections.
- In the commands control sent above the control connection, file transfer occurs on the data connection.
- The client must specify the type of file being transferred, its data structure, and its mode of transmission at all times.
Characteristics
The characteristics of file transfer protocol include the following.
- FTP only uses TCP as the transport protocol.
- Port number 21 is used by this protocol for control connections.
- This protocol is considered out-of-band since data and control information cross multiple connections.
- The port number 20 is used by this protocol for data connections.
- This type of protocol makes use of ongoing TCP connections for the control connection.
- It employs non-persistent connections for data connections.
- It is a protocol that is connection-oriented.
Features
The features of file transfer protocol include the following.
Representation of Data
This protocol simply handles three kinds of data representations like ASCII, EBCDIC & 8-binary data
File Organization & Data Structures
This protocol supports both structured as well as unstructured files.
- A structured type file includes a records list where every record is surrounded by End of Record. So data structure of such files is known as record structure.
- An unstructured type file includes a series of bytes which is enl-marked through the End of the file. So data structure of such a file is known as file structure.
Transmission Modes
- File stream mode, block mode, and compressed mode are the three transmission modes used by FTP.
- A default mode is referred to as stream mode. The file is simply sent as a steady stream of bytes to TCP in this manner. TCP is therefore responsible for segmenting data into appropriate size chunks.
- In block mode, data is transferred from FTP across TCP in blocks, each of which has a three-byte header. The first byte is the block descriptor, and the second and third bytes are just used to specify the block size in bytes.
- If the sent file is large, it is often compressed in compressed mode.
Error Control
There is no need for an additional error recovery device because TCP is used for data transfer.
Access Control
By submitting login information during the login process, file access is protected.
Advantages and Disadvantages
- Multiple files and directories are possible with this protocol.
- FTP is significantly faster than HTTP.
- The speed of file transfers is quite swift.
- It works with almost all hosts.
- A synchronization tool is typically included with clients.
- A transfer can be scheduled in FTP clients.
- no size restriction on individual transfers.
- Many users have access to scripting features through a command line.
- the ability to add objects to a line that can be downloaded and uploaded.
- FTP provides a built-in backup feature.
The disadvantages of the file transfer protocol include the following.
- Login information and files are provided in clear text.
- Encryption is not a service that is given by default by any provider.
- It is simple for a novice user to ruin work.
- TLS 1.2 is not always supported over HTTPS.
- On your own workstation, screening active FTP connections is really challenging.
- This protocol is not secure.
- FTP is vulnerable to attack
- A challenge is a compliance.
- Checking activities is really challenging.
Applications of File Transfer Protocol
- Business-to-business and peer-to-peer data transfer are two common daily business activities where file transfer protocol is used:
- Organizations utilize the FTP protocol because it enables employees to divide files among multiple locations and branch offices.
- This protocol is used to send files securely between coworkers and outside business partners.
- IT teams utilize this type of protocol to send data back to DR (disaster recovery) facilities.
- This protocol is used by webmaster teams to upload web pages, photos, and web application files to their web server.
- Other medium-sized and small enterprises, including those in the fields of architecture, construction, civil engineering, printing, transcription, IT & business consulting, media, marketing, and legal & financial services, employ this protocol.
Conclusion
I hope all of you understand the basics of File Transfer Protocol: Working, Types & Its Applications. We MATHA ELECTRONICS will be back soon with more informative blogs.
